Security researchers at ESET have released a report concerning a new type of malware found on the Google Play Store that appears to use a sophisticated means of flying under the radar to avoid detection. The malware in question was dubbed Android/TrojanDropper.Agent.BKY and eight apps were found in the Google Play Store containing the malicious code.

Google has removed all eight apps from the store and researchers point out that the removed apps only had a few hundred downloads a piece, so this wasn’t as large a spread as some of the previous malware invasions we’ve reported on. ESET notes that this malware family’s specific anti-detection features are the most interesting part of the story.
Once the apps were downloaded and installed, they don’t request suspicious permissions and the app even performs as the user would expect. The app instead decrypts and executes several different payloads in a type of Russian nesting doll code execution in an effort to obfuscate the malware’s true purpose. Check out this basic outline of how the malware gets unaware users to install a truly malicious app while bypassing Google’s security checks.
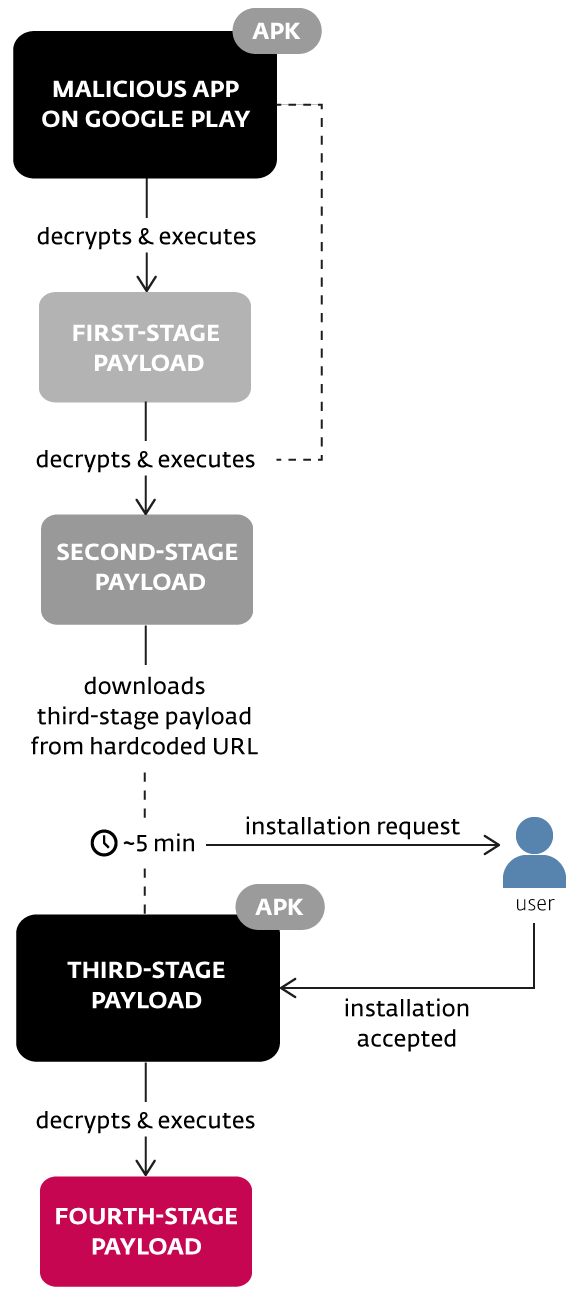
Researchers note that the app that’s downloaded and executed by the second-stage payload is usually disguised as a well-known product like Adobe Flash Player or simply “Android Update.” Once this app gets all the permissions it needs to install the fourth payload, researchers found a banking trojan that attempts to phish usernames and passwords.









Comments